Check for Netlogon Events Related to CVE-2022-38023
Microsoft will force the Netlogon configuration changes in June 2023 (see link below). You should check every Domain Controller's System EventLog to look for these events. If you find any, you'll want to remediate them before June 2023.
Use the Windows EventLog to Discover the Netlogon Events
Target a Domain Controller and Open the System Windows EventLog. On the far right side of the EventLog window, select the Action: Filter Current Log... 
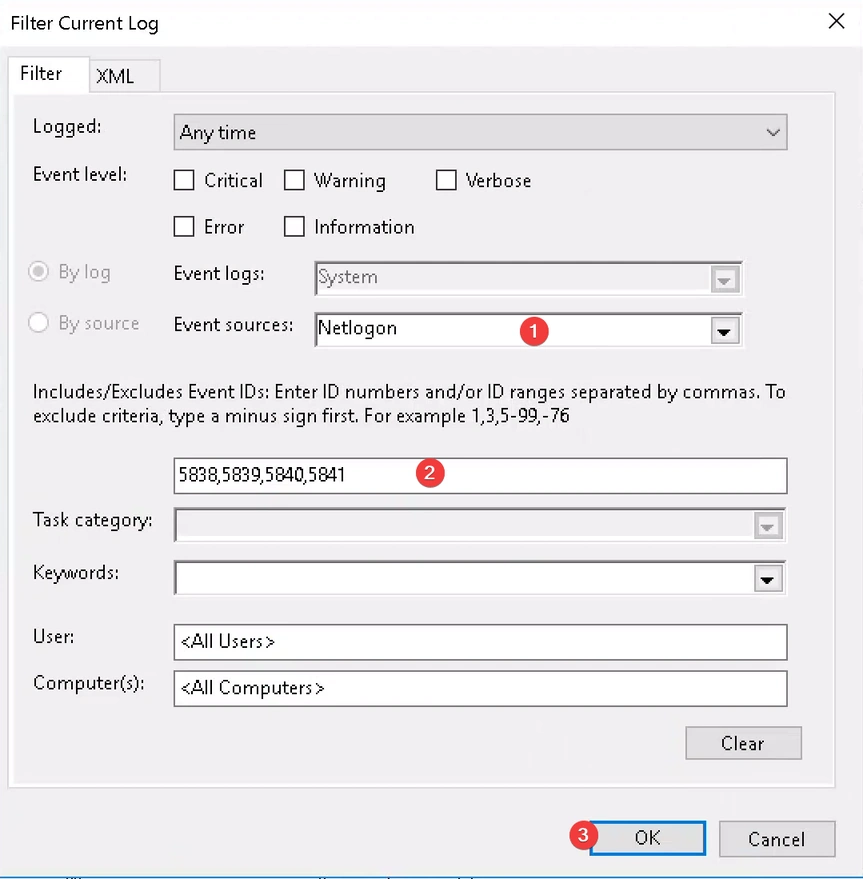 You only need to modify two items:
You only need to modify two items:
- Event sources: Netlogon
- Event IDs: 5838, 5839, 5840, 5841 1
- Click the OK button
Use PowerShell to Query the Windows System EventLog
1# Setup our timediff variables
2[uint32]$SecondsInDay = 86400
3[uint16]$MillisecondsOneSecond = 1000
4[uint32]$MillisecondsOneDay = $SecondsInDay * $MillisecondsOneSecond
5[uint32]$Milliseconds7Days = $MillisecondsOneDay * 7
6[uint32]$Milliseconds30Days = $MillisecondsOneDay * 30
7
8# The Windows EventLog uses milliseconds to do timediff
9[string]$Last30Days = @"
10<QueryList>
11 <Query Id="0" Path="System">
12 <Select Path="System">*[System[Provider[@Name='Netlogon'] and (Level=2 or Level=3) and (EventID=5841 or EventID=5840 or EventID=5839 or EventID=5838) and TimeCreated[timediff(@SystemTime) <= $($Milliseconds30Days)]]]</Select>
13 </Query>
14</QueryList>
15"@
16
17# Group by Account Name and sort by Count (ascending)
18(($Events30Days | Where-Object {$_.Id -eq 5840} | `
19 ForEach-Object {$_.Properties.Value[0]}) | `
20 Group-Object) | `
21 Sort-Object Count
22
23# Iterate over the events and process them
24ForEach ($evt in $Events30Days) {
25 switch ($evt.id) {
26 5838 { }
27 5839 { }
28 5840 {
29 " Account Name: $($evt.Properties.Value[0])"
30 " Domain: $($evt.Properties.Value[1])"
31 " Account Type: $($evt.Properties.Value[2])"
32 " Client IP: $($evt.Properties.Value[3])"
33 "Negotiated Flags: $($evt.Properties.Value[4])"
34 }
35 5841 { }
36 # should never get this since our event filter doesn't ask for it
37 Default {Write-Warning "Unknown event '$($evt.id)'"}
38 }
39}